11:25 AM
Anti-Malware Doesn�t Cut It in the Mobile Era
It’s no secret that retailers are under attack. Not from masked robbers, but from anonymous criminals that work online. What is less widely known is that anti-malware -- the virtual guardian of the PC era -- won’t protect organizations in an increasingly mobile world. And the pace of change in mobile is so great that certain security standards can quickly become obsolete.
To address the rapidly changing challenges in mobile security, I have had the privilege of working with the Payment Card Industry (PCI) Security Standards Council as part of its PCI Mobile Task Force. We are focused on the emerging mobile point-of-sale (POS) technologies and the evolving mobile threat landscape. As more retailers deploy mobile devices for mobile POS, mobile presents the opportunity for more automated security countermeasures for protecting retailers from attack. Therefore the PCI Mobile Task Force continues to update the PCI guidelines to take advantage of these unique security features.
Learning from recent attacks
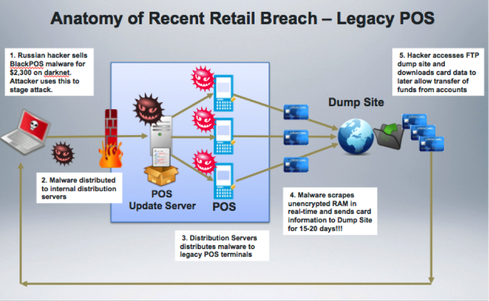
Recent retail breaches exposed a common theme with the attacks that involve infecting legacy POS devices. It demonstrates a lack of defense-in-depth strategies within these legacy POS environments.
The nice thing about mobile POS is that when an organization incorporates enterprise mobility management (EMM) and mobile into a retail environment, it comes with a full defense-in-depth strategy. Any holistic security strategy should include both proactive and reactive countermeasures. EMM and mobile enables that in a variety of ways:
Sandboxes make antimalware irrelevant
After analyzing more than 2.5 million apps for our mutual enterprise customers, Appthority found that less than half a percent were malware. Appthority is an app reputation service that integrates with MobileIron’s EMM dashboards.
Traditional anti-malware (especially anti-virus) are becoming less relevant in the mobile era. This is because operating system architectures are shifting from open file systems (Windows 7 and below) to application sandboxes (Android, iOS, Windows Phone/Pro/RT).
For example, on iOS, there isn’t much for anti-malware or anti-virus products to do because neither they nor any other app on the device can access another app's storage or memory. On Android, there is some shared storage and memory, and so there are anti-malware and anti-virus products. But these products only detect and alert, so even on Android, they don't mitigate or remediate the problem once detected, because they can't remove a bad app.
The EMM alternative
The basic difference between anti-malware and enterprise mobility management is that anti-malware for mobile is reactive and doesn’t mitigate the problem once detected. EMM provides both proactive countermeasures and reactive mitigation.
EMM proactive and automated mitigation measures include managing app, content, and device access and creating automated countermeasures for when devices fall out of compliance with security policies. This includes:
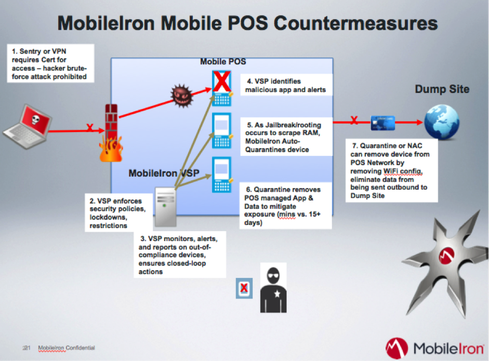
Mobile POS proactive and reactive automated protection. Mobile POS (mPOS) can be further protected by EMM. For example, EMM solutions can distribute the mPOS app to the device. This therefore enables management of the app to enforce control over that app. If a nefarious attack occurs, or the device falls out of compliance (jailbreak, root, disabled PIN, etc.), the auto-quarantine kicks in and can block network connectivity or remove the mPOS app and its data, thus mitigating a breach. In the case of recent retail breaches, the window of compromise occurred for weeks or months with legacy POS devices. With mobile and EMM, organizations can detect malicious apps, as well as when a jailbreak or rooting occurs, and can respond in a matter of hours or minutes. It’s also important to note that this mitigation is automated without the need for a human in the loop. This can mitigate the threat automatically and minimize the window of compromise.
Certificates. The PCI Data Security Standards (DSS) 3.0 requirements outline the use of certificates for authentication for WiFi and for remote access. EMM enables this by providing a built-in Certificate Authority and automated distribute of certificates to mobile devices. This deters man-in-the-middle attacks and eliminates passwords, which can be vulnerable to brute-force attacks. This also helps organizations achieve compliance with the Mobile Payment Acceptance Security Guidelines v1.0, Objectives 1, 2, and 3, released in Sept. 2012.
App containerization. App containerization operates through a software development kit (SDK) or app wrapping to separate corporate and personal data so that even if malware is downloaded to the device, the isolated corporate data remains intact and unaffected. It enables enforcement of data loss prevention (DLP) rules to restrict content sharing with unauthorized apps on the device
App reputation service. Anti-virus and anti-malware are largely ineffective in mobile due to the application sandboxing in iOS, Android, and Windows Phone 8. Arguably the best that these products can accomplish is to possibly identify malicious, rogue, or risky apps. In contrast, an app reputation service in conjunction with EMM can provide a variety of detection as well as countermeasures and quarantine options to remove the human-in-the-loop and automated mitigation:
- Consistent security policies applied to corporate data such as email, apps, documents, and web pages
- Device-level lockdown policies when tight control is required
EMM reactive mitigation measures include:
- Auto-quarantine ranging from a simple blocking of email to an automated selective wipe of the corporate data and apps to avoid a breach. This action can be triggered by a malware download or a jailbreak/rooting action, and the security action knob can be adjusted by the administrator.
- Integration with app reputation services that monitor the inventory of apps on the device to flag those with undesirable or risky behaviors and trigger a notification, access control, quarantine, or wipe action.
Put another way: Where do EMM solutions overlap with mobile security services from the top anti-virus vendors? There is very little overlap, and they take completely different approaches. Traditional security products were built for the security issues of Windows. Mobile architectures are different.
Protection at the speed of mobile
EMM solutions approach mobile security in a different and more complete way than traditional anti-malware solutions do. An enterprise won’t be able to secure mobile apps, content, and devices using only an anti-malware solution. There might be times when enterprises wish to distribute an anti-malware app through EMM to provide additional security, and anti-malware can provide some complementary controls on certain devices, but EMM is quickly becoming the primary approach to protect cardholder data on mobile.